Key Benefits and Intelligent Features
Abnormal Security combines advanced behavioral AI with automated threat prevention to deliver powerful protection against today’s most sophisticated email threats. From detecting subtle anomalies to simplifying response and remediation, every feature is designed to strengthen your defenses while reducing the burden on your security team.
Behavioral AI-Powered Threat Detection
Ingests identity, behavior, and content signals to detect advanced threats like BEC and VEC by identifying subtle anomalies.
One-Click API Integration
Fast, seamless deployment with simple integration into existing email and SaaS environments.
Automated Threat Prevention and Response
Automatically remediates malicious emails, reducing SOC triage and operational workload.
Explainable Detection Outcomes
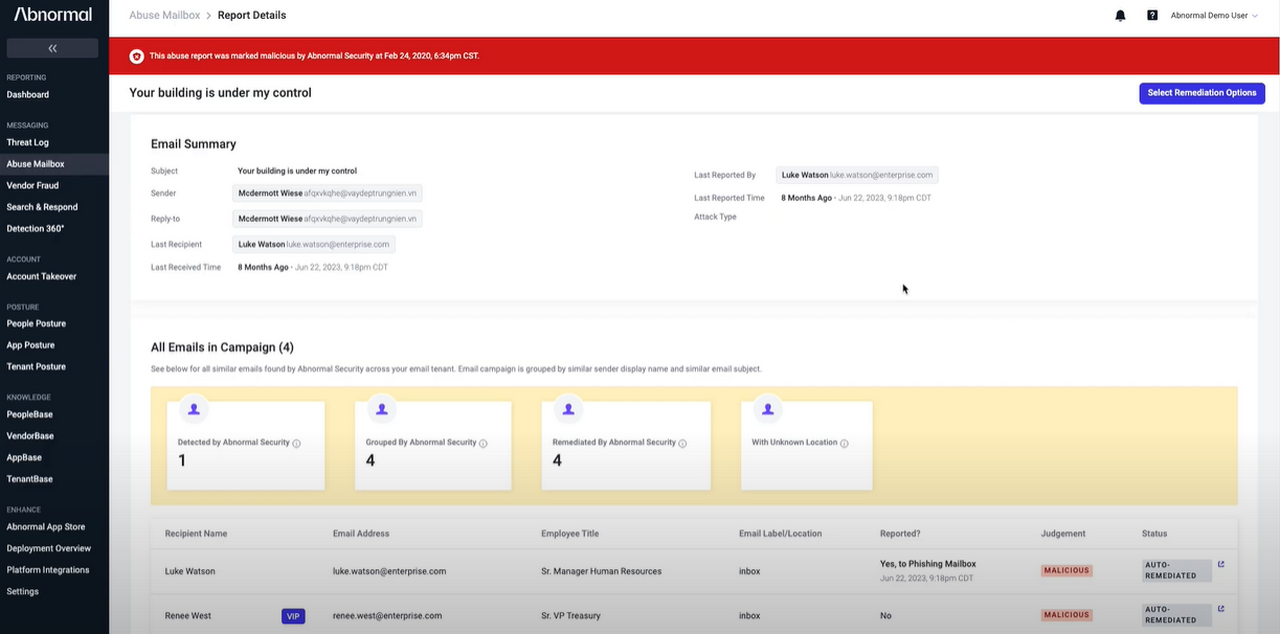
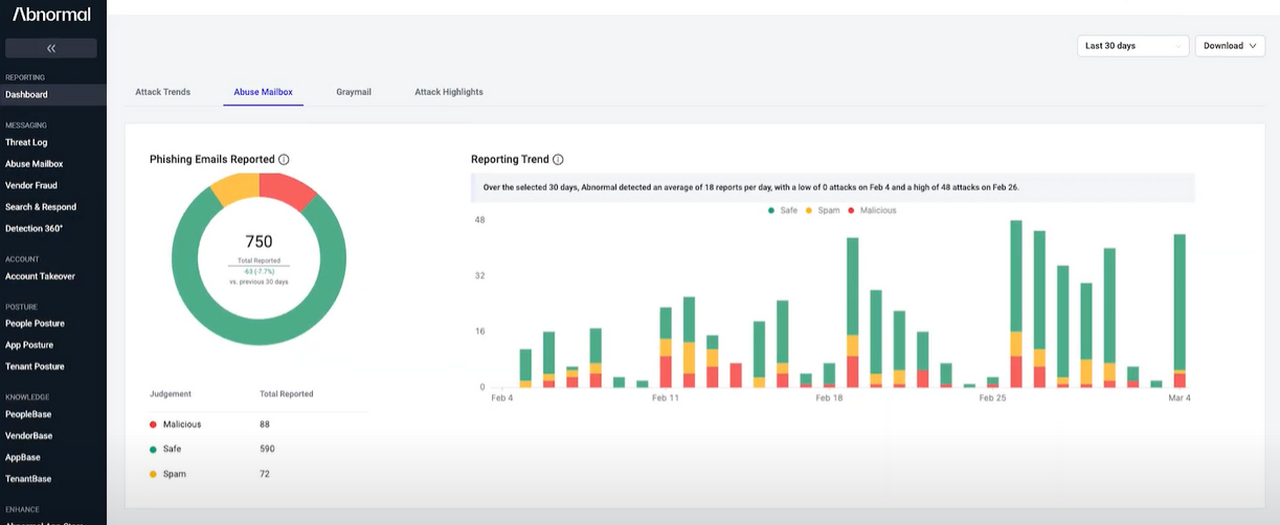
Provides detailed logs, visual timelines, and enriched metadata for full transparency and easier investigations.
Customizable Security Controls
Admins can tailor risk thresholds, remediation workflows, and quarantine actions to match organizational needs.
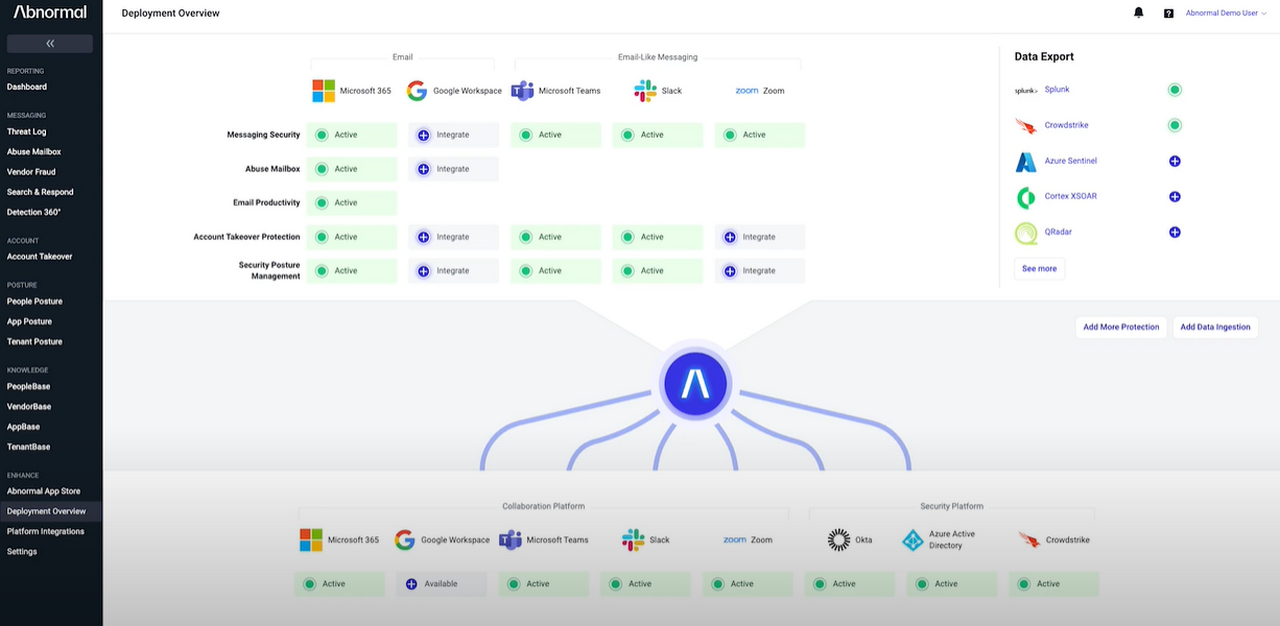
Unified Threat Management Console
Centralizes threat visibility and response across Microsoft and Abnormal detections.
SOAR Integration
Connects with SOAR platforms to streamline and automate incident response workflows.
Adaptive and Continuous Learning
Continuously evolves using behavioral data, attack trends, and cross-tenant intelligence—no manual rule writing required.
Business Email Compromise (BEC) Detection
Identifies targeted BEC attacks by analyzing sender behavior and communication history.
Vendor Email Compromise (VEC) Detection
Monitors vendors for suspicious activity, even from trusted domains, to block supply chain attacks.
Human Behavior AI
Establishes baselines for every employee and vendor to detect even minor deviations in behavior.

